When using the Mission Control SaaS the agent based approach is recommended for ingesting data, The agent is headless installation of mission-control that caches data locally in a postgres database and replicates it to the SaaS.

The agent based approach has the following benefits:
- Least privilege, as the agent runs within your infrastructure there is no network access or credentials required to be configured on the SaaS.
- CRD Based Configuration of health checks and scrape configs co-located with your IaC/App without the need to push any config to the SaaS.
- Local Playbook Execution on agents, reusing existing secrets or IAM roles.
See Deployment Models for Self Hosted and Fully Hosted options
Signup
a. Goto app.flanksource.com/signup to signup
b. Choose an organisation name and logo
c. Invite your team members
Organization details and members can be changed by going to accounts.flanksource.com/organization or Clicking on Manage Organization when logged in
Agent Installation
To install and run the Mission Control agent you need to have the following prerequisites:
- Kubernetes v1.27+ and Helm v3
- 1 - 2 CPU cores and 4GB of Memory
- Persistent Volumes with 10GB+ of storage or an external postgres database like RDS.
a) Click on Settings → Agents in the sidebar.

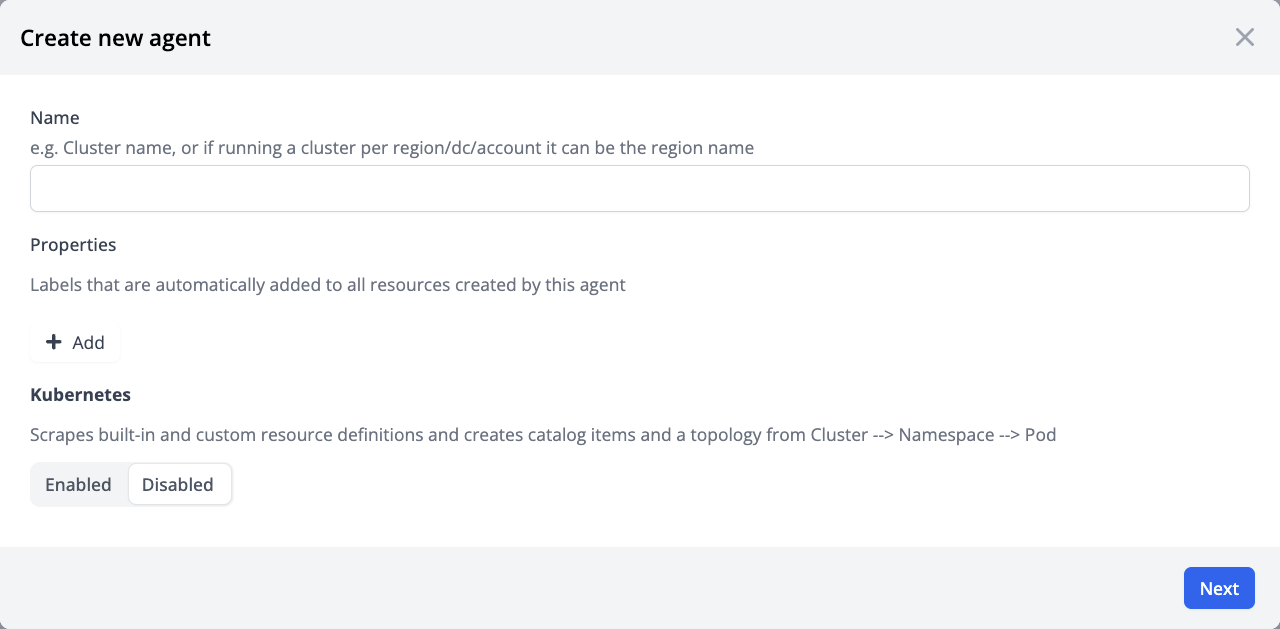
c) Enter an agent name - This can a cluster name, or an account name (for hub-spoke clusters).
Keep the agent name short and unique as it is used as a tag when displaying resources from this agent in the UI.
d) Click on Next
The wizard will create a new agent token with instructions for installation via Helm CLI or FluxCD manifests.
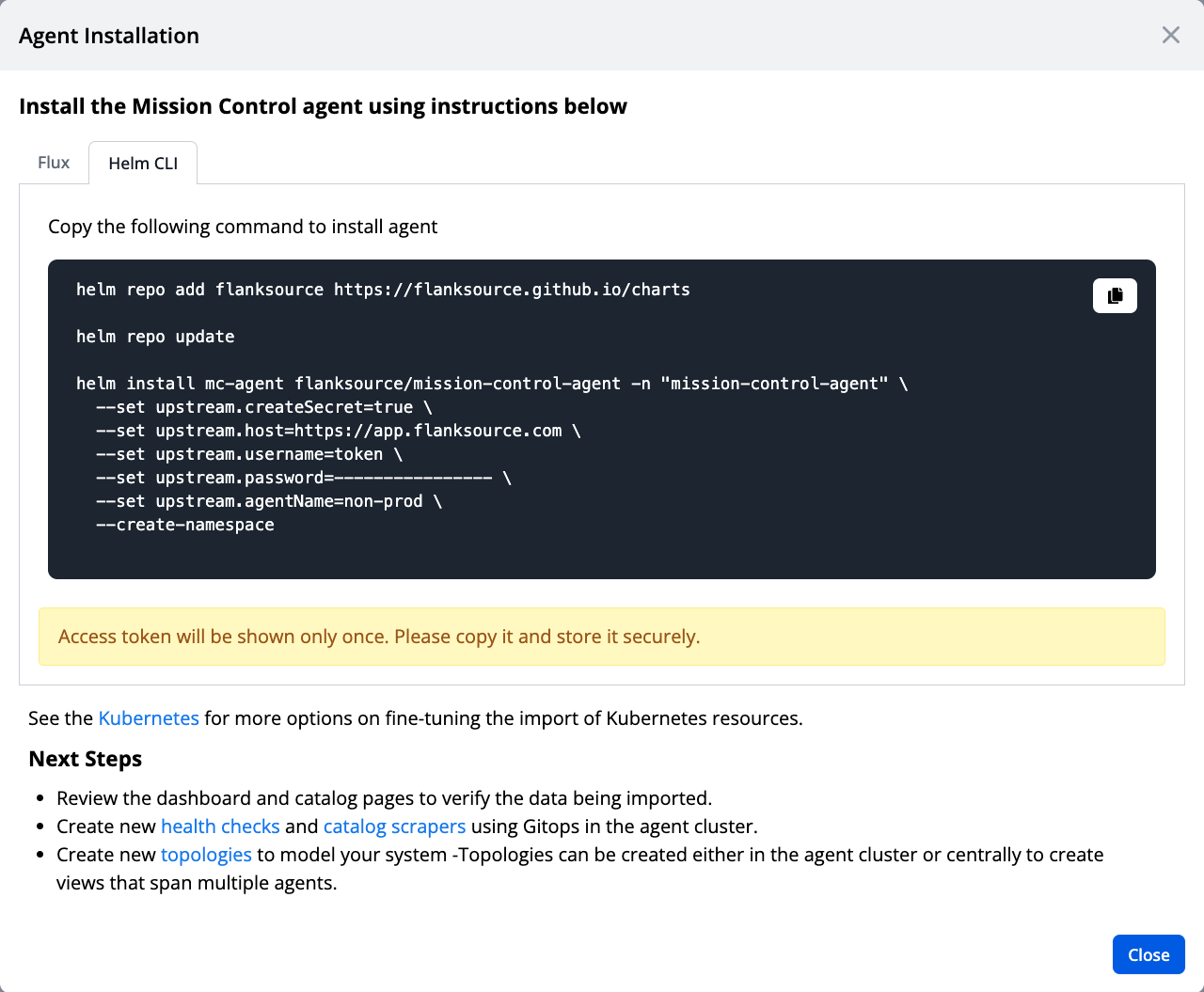
Flux Installation
apiVersion: v1
kind: Namespace
metadata:
name: mission-control-agent
---
apiVersion: source.toolkit.fluxcd.io/v1beta1
kind: HelmRepository
metadata:
name: flanksource
namespace: mission-control-agent
spec:
interval: 5m0s
url: https://flanksource.github.io/charts
---
apiVersion: helm.toolkit.fluxcd.io/v2beta1
kind: HelmRelease
metadata:
name: mission-control
namespace: mission-control-agent
spec:
chart:
spec:
chart: mission-control-agent
sourceRef:
kind: HelmRepository
name: flanksource
namespace: mission-control-agent
interval: 1m
values:
upstream:
createSecret: true
host: https://app.flanksource.com
username: token
agentName: non-prod
password:----------------
It is highly recommended to encrypt the token and reference it as a secret:
...
spec:
valuesFrom:
- kind: Secret
name: mc-token
valuesKey: password
targetPath: upstream.password